Booking.com Scam by Russian Cybercriminals Puts US Hotels at Risk
Table of Contents
ToggleIn a worrying development, scammers are now targeting the hospitality industry with a sophisticated phishing scam designed to steal sensitive information and potentially compromise hotel operations. The attack masquerades as legitimate communication from Booking.com, fooling hotel staff into interacting with fake guest inquiries. This article uncovers the inner workings of this scam, its alarming Russian connection, and practical steps hotels can take to defend against these attacks.
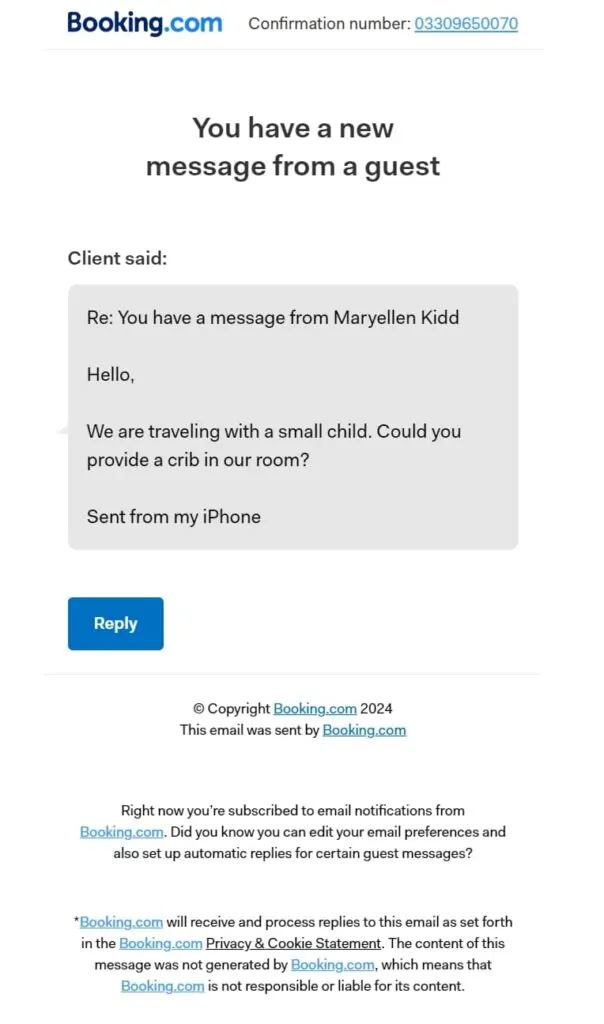
If you’re in the hotel business, this is a must-read to safeguard your operations from falling prey to cybercriminals.
How the Scam Works: The Anatomy of the Fake Email
The scam starts with a convincing email sent to hotel staff, appearing to be from Booking.com. Here’s what makes it so deceptive:
- Fake Guest Inquiry:
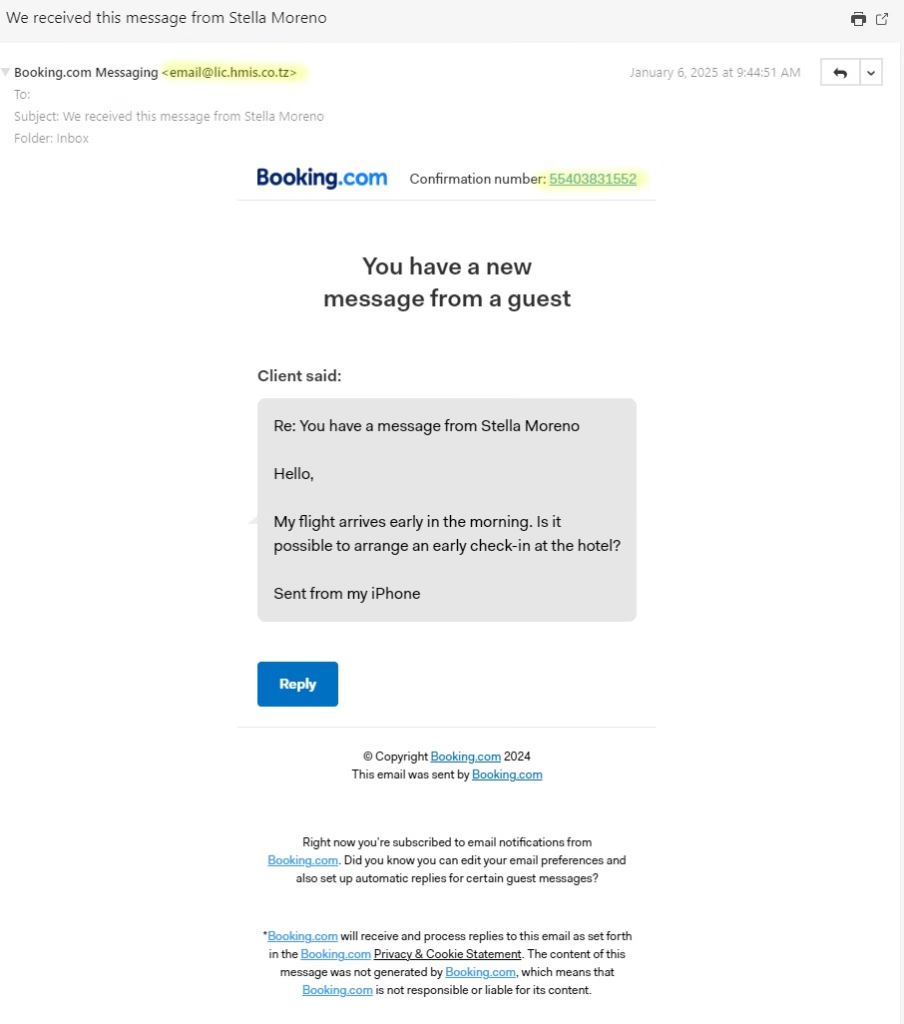
The email contains a seemingly legitimate message from a “guest” asking about their stay. For example:
“Hello, my flight arrives early in the morning. Is it possible to arrange an early check-in at the hotel?” - Professional Layout:
The design of the email mimics Booking.com’s branding, including a confirmation number and a “Reply” button, creating an illusion of authenticity. - Bit.ly Link Tracking:
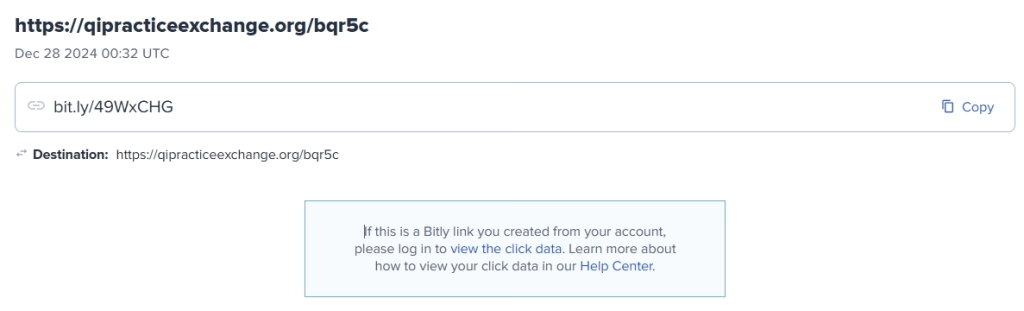
Upon inspection, the “Reply” button or confirmation number contains a bit.ly shortened link. Scammers use this to hide the destination URL and track if someone has clicked on the link.
Bitly URL Decoding - Malicious Redirect:
Using a Bitly Decoder Tool, investigators found that the link redirects to a suspicious website:https://qipracticeexchange.org/bqr5cWhois data reveals that the site is hosted on a server in Russia, registered under Network Solutions, LLC.
Key Findings from the Whois Lookup
Here’s what we uncovered about the fake domain, qipracticeexchange.org:
- IP Address: 193.3.19.63
- Hosting Location: Moscow, Russian Federation
- ASN: Hosted under JSC Selectel, a Russian-based infrastructure provider.
- Domain Age: Registered on February 22, 2011, but its recent activity suggests it was repurposed for malicious use.
- Name Servers: Managed by DNSMadeEasy, often used to set up websites quickly.
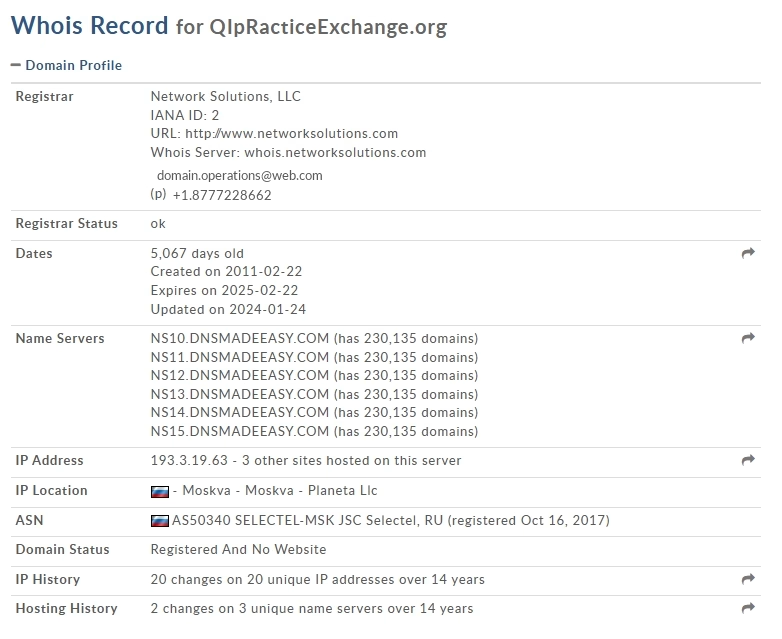
This information highlights that the operation may originate from Russia, targeting US-based businesses, especially hotels.
Why Hotels Are Being Targeted
Hotels are a lucrative target for cybercriminals because they handle large volumes of sensitive guest data, including:
- Credit card information
- Personal identification (passport numbers, etc.)
- Internal booking systems
By gaining access to hotel systems, scammers can commit fraud, steal valuable data, or even disrupt operations by infecting networks with malware.
Red Flags to Watch Out For
- Unusual Sender Email Address:
- The scam email originates from domains like
email@lic.hmis.co.tz, which do not belong to Booking.com. Always check the sender’s address carefully.
- The scam email originates from domains like
- Shortened URLs:
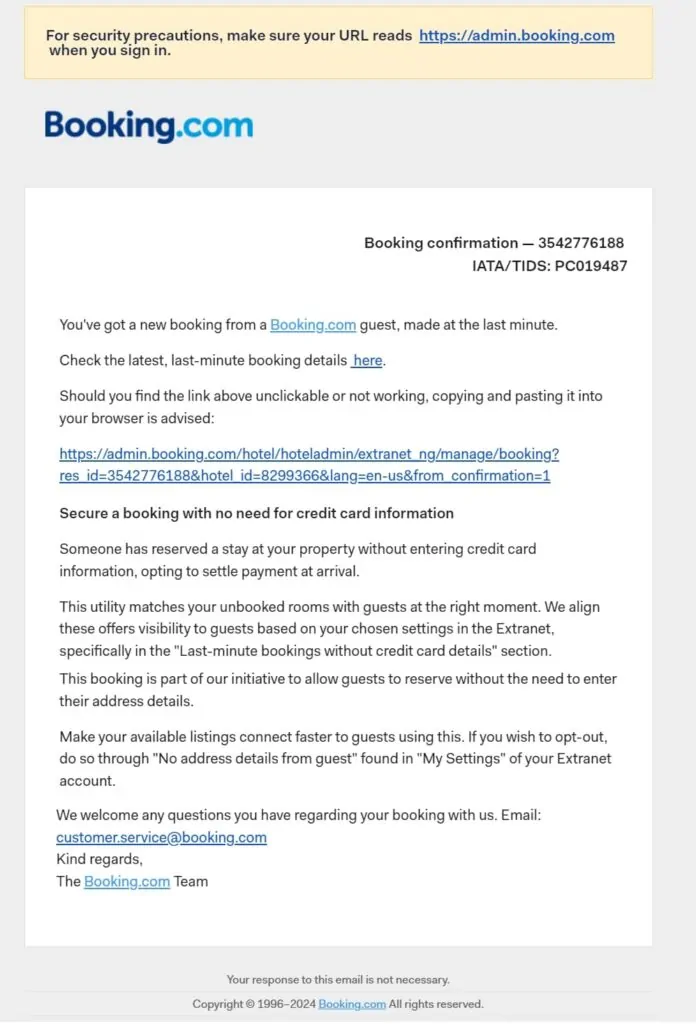
- Legitimate businesses rarely use services like Bit.ly in emails. Suspicious shortened links can be decoded using tools like Bitly Decoder to reveal the true destination.
- Urgent Yet Simple Requests:
- Asking for early check-ins, confirmations, or immediate replies is a tactic to build trust and prompt quick action.
- Foreign Domains:
- Domains hosted on Russian servers or unfamiliar registrars should be treated with caution.
How to Protect Your Hotel from Scams
- Verify the Sender:
- Check if the sender’s email matches Booking.com’s official domain (e.g.,
@booking.com). Look for slight variations or odd endings.
- Check if the sender’s email matches Booking.com’s official domain (e.g.,
- Inspect Links Before Clicking:
- Hover over links to see the destination URL. Use tools like Bitly Decoder to verify the legitimacy of shortened links.
- Use a Whois Lookup Tool:
- Investigate any suspicious domain to see its registration and hosting details. If it’s hosted in a high-risk country, proceed with caution.
- Educate Staff:
- Conduct regular training for hotel employees to identify phishing emails, suspicious domains, and other red flags.
- Implement a Secure Email Gateway:
- Use email security tools that filter out phishing and spam emails.
- Report the Scam:
- Notify Booking.com directly if you receive a suspicious email claiming to be from them. Report the phishing attempt to relevant authorities, such as Google Safe Browsing or IC3.gov.
Breaking Down the Russian Connection
A deeper analysis of the scam’s infrastructure revealed that the domain qipracticeexchange.org is hosted on servers located in Moscow, Russia, and maintained by Planeta LLC. The scammers have repurposed an old domain, leveraging its aged credibility to bypass spam filters. This level of planning indicates a well-organized operation targeting US-based hotels.
Furthermore, the use of bit.ly links allows the attackers to monitor which recipients have clicked, narrowing down their targets for further exploitation.
FAQs About the Fake Booking.com Scam
1. How can I tell if an email from Booking.com is real?
Check the sender’s domain carefully. Booking.com emails always come from @booking.com. Avoid interacting with any email from an unfamiliar address.
2. What should I do if I clicked a suspicious link?
Immediately disconnect from your network, run a malware scan on your system, and notify your IT department. Change any passwords associated with your Booking.com account.
3. Are bit.ly links always unsafe?
No, not all bit.ly links are harmful. However, they can obscure the destination URL, making them a favorite tool for scammers. Always decode shortened links before clicking.
4. What action should I take if I suspect an email is a scam?
Forward the email to Booking.com’s support team for verification. Avoid clicking on any links or downloading attachments.
5. Why are hotels specifically targeted?
Hotels handle valuable data, including credit card details, making them attractive to scammers. Phishing scams exploit hotel staff’s trust in communication systems like Booking.com.
6. Can these scams infect my hotel’s booking system?
Yes. Clicking on malicious links may install malware or give attackers access to internal systems. This can lead to data breaches or financial fraud.
Conclusion
Cybercriminals are constantly evolving their tactics, and the recent fake Booking.com email scam is a chilling example. By targeting hotels with cleverly crafted phishing emails, they exploit the trust that staff place in recognized platforms.
Staying vigilant, verifying sender information, and using security tools are crucial steps to defend against such threats. Don’t let your hotel become a victim—educate your staff, report suspicious activity, and always think twice before clicking.